What is a VLAN?
Firstly, a LAN simply denotes devices that are connected to a shared broadcast domain. The broadcast domain is defined by the devices that will receive a broadcast frame with MAC address ff:ff:ff:ff:ff:ff. For example, let's look at the below diagram:
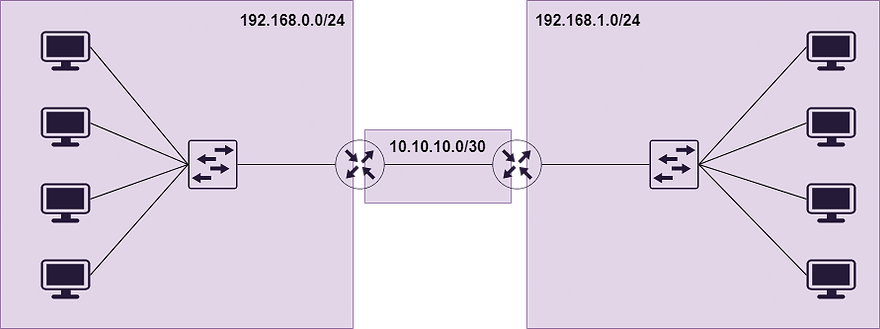
Each purple box is a separate broadcast domain as they share the same subnet. Note that the point to point link between the routers is also a broadcast domain. All devices within each subnet will receive broadcast frames, and the switch facilitates this by flooding these frames out of all ports. Even if there are multiple switches in the same subnet they are still part of the same broadcast domain.
Let's now imagine there are 6 48-port switches within the local network and each switchport is fully utilised. This is going to generate a lot of broadcast traffic and also from a security perspective every device is reachable directly within the same network. For example if someone from accounting has an infected PC the malware can easily spread across the network. To resolve this we need to segregate devices as much as possible to reduce the amount of broadcast traffic and reduce the impact of a device getting infected on the network. To do this we use VLANs (Virtual Local Area Network). VLANs allow for a logically split layer 2 network, each with it's own network range and uses a VLAN ID for the switch to identify which frame is in which VLAN. Clients are typically not VLAN aware and usually all VLAN processes are completed on the network devices.
NBProducts Ltd. has 30 devices within their head office, shared across multiple departments. To ensure the network is fully optimised the network administrator has divided the network into multiple VLANs to segregate the network. See below:

By using VLANs, if there is no routing between them on the router devices in HR cannot reach devices in Sales or Accounting. Should a malicious user access the network 192.168.2.0/24 in accounting, it is now much harder for them to reach a device within the HR department as the network is segregated at layer 2. Broadcast frames will not be forwarded between VLANs, making the network more efficient. In the extended VLAN range there can be a maximum of 4094 VLANs.
In order for VLANs to work, we need to understand the different port types that facilitate VLANs within the network, access ports and trunks. Read about them below.
Access Ports
Clients are not VLAN aware, and this action of segmenting the network is performed at the point at which the client connects to the network, which is usually a switch. As the frame comes into the switch from the client device, the switch will only forward the frame to other interfaces in the same VLAN or in the case of unknown unicast/broadcast, flood the frame out of all matching access ports.
If we use our example from above where we had 3 VLANs (10, 20 and 30) we would set each port to "switchport mode access", and then define the VLAN ID for the switchport as "switchport access vlan [ID]". So for VLAN 10, we would use the below commands:
conf t
interface Fa0/0/1
switchport mode access
switchport access vlan 10
exit
exit
If we were to apply the above config to each port (changed the VLAN ID as required) then the topological view of the switch would look something like this:

If we were to plug a client PC into port Fa0/0/1, it would only be able to communicate with other ports designated as access VLAN 10. If the user needed to reach another client on a different VLAN, the traffic will have to be forwarded to the router. This is known as Inter-VLAN Routing.
Note how the final three switchports are highlighted, this is to denote the interfaces used by the router. If we had multiple switches this would mean a large number of interfaces would be used just for forwarding traffic from clients to the router. We can minimise the amount of required ports by using 802.1q (dot1q) trunk ports. See below.
**Please note that access ports are sometimes referred to as untagged ports, particularly by other vendors.**
Trunk Ports (802.1q)
Trunk ports are used when multiple VLANs need to be carried across a link, say between switches or up to a router. Rather than using 3 separate physical interfaces, we can concatenate inter-switch links or uplinks to routers into a single interface. As you can see in the below diagram, if we didn't use trunk ports we would have to use 3 interfaces on the router and the bottom switch, and 6 interfaces on the middle switch. This is very wasteful as it reduces the number of interfaces available to client devices, it's simply not scalable.

When interfaces are set to trunk, it adds a section to the Layer 2 frame header which is referred to as tagging. We need to add this section to the frame header because without it, the switch or router on the other end of the trunk isn't aware of which access port the frame originally arrived from. If we look at the below diagram we can see how the 802.1q tag works and what information it contains.

-
Tag Protocol Identifier - signals to the receiving appliance that the frame is tagged with 802.1q, it always has the value of 0x8100 (hexadecimal)
-
Priority Code Point - Used for Class of Service
-
Drop Eligible Indicator - Indicates whether a frame can be dropped if there is congestion on the network
-
VLAN ID - Value between 0 and 4095 and identifies the VLAN that the frame belongs to (0 and 4095 are reserved, allowing 9094 VLAN IDs)
So, if we go back to our network diagram above, let's say that a PC in the Sales VLAN sends a broadcast packet out into the subnet on SW2. The frame arrives from the PC into the switch via an access port in VLAN 10. The switch forwards the frame out of all VLAN 10 access ports, but also the trunk port. As it exits the trunk port the switch adds the 802.1q tag with VID 10. This means that when SW1 receives the frame and de-encapsulates it, it knows that the frame originated from VLAN 10 and can forward the frame to the VLAN 10 access ports on SW1 including the trunk port between SW1 and RTR1.
To configure a trunked interface, we use the below commands. Note that both interfaces on each side of the link must be configured as trunk ports.
conf t
interface Fa0/0/1
switchport mode trunk
switchport trunk encapsulation dot1q
exit
exit
There are also other configurations to further scope the trunk port to the requirement, such as allowing specific VLANs. For example:
conf t
interface Fa0/0/1
switchport trunk allowed vlan 10,20,30
exit
exit
Default VLAN
The default VLAN is the initial VLAN that is created during device provisioning. For Cisco appliances, this is VLAN 1. All switchports by default are set to VLAN 1.
Native VLAN
So far we have covered what happens when traffic enters the network on an access port and how VLANs traverse a trunked port using the 802.1q tag, but another important concept that we need to cover is the native VLAN. Simply put, the native VLAN is used where traffic traverses a trunk port without a VLAN tag. This is referred to as 'untagged' traffic.
The configuration for the native VLAN must match on each side of the trunk port, and it is also recommended to set a different native VLAN ID from any other VLANs on the network. For security reasons, always change the native VLAN ID from the default ID of 1.
The native VLAN differs from the default VLAN. It's easy to confuse the two but just remember that the native VLAN only relates to untagged traffic across a trunk link, whereas the default VLAN is the default VLAN ID assigned to all access ports (VLAN ID 1).
Voice VLANs
This is a relatively simple concept. Most offices use IP Desk Phones and a workstation/laptop for their employees to do their jobs. Rather than using a separate network cable for both the IP Phone and the PC, we can leverage voice VLANs to connect both devices to a single interface on the switch. The IP phone itself also has a small built in switch to keep the PC and telephony traffic separate. This reduces the number of patch ports, network switches and cable management required to connect each desk to the network. See below:

As you can see we have halved the number of cables required per desked user, which in turn reduces overall cost of networking equipment and administrative overhead by running additional wiring.
To configure a voice VLAN, simply add the following example line to the switchport interface config:
conf t
interface Fa0/2
switchport mode access
switchport access vlan 10
switchport voice vlan 100
exit
exit
Router on a Stick (ROAS)
Devices between VLANs cannot communicate with one another as they are segregated at layer 2. To facilitate Inter-VLAN routing, we can use the Router on a Stick topology to allow devices between VLANs to communicate with one another on layer 3. We can do this by sub-interfacing the physical interface, which allows for multiple IP addresses and configurations to be added to a single physical interface. You can identify a sub-interface easily as it includes the physical interface ID, with the sub-interface ID being appended following a full stop. So if we were to create 3 sub-interfaces on Gi0/1 it will look like this:
Gi0/1.100
Gi0/1.200
Gi0.1.300
Let's take the topology that we used above for 802.1q trunk ports. Instead of configuring the interface on the router as a trunk, we sub-interface the physical port for each VLAN. This adds each network into the routing table of the router and allows traffic to pass between VLANs. We use the encapsulation dot1q command within the sub-interface to allow the trunking between the switch and the router to take place. Let's see how it works from a configuration perspective:

Router and Switch Configuration for Router on a Stick Topology

Now that we have added these sub-interfaces, we can see that they have been added to the routing table:
RTR1#show ip route connected
C 192.168.1.0/24 is directly connected, GigabitEthernet0/1.10
C 192.168.2.0/24 is directly connected, GigabitEthernet0/1.20
C 192.168.3.0/24 is directly connected, GigabitEthernet0/1.30
So if say a PC on VLAN 10 wants to send traffic to a PC on VLAN 30, the router will forward the traffic back out over sub-interface Gi0/1.30 as the destination IP will be within that subnet.
Switched Virtual Interfaces (SVI)
In larger networks, the Router on a Stick topology can become a bottleneck, as all traffic between VLANs must ingress and egress out of the router. To make the network more efficient we can leverage Switched Virtual Interfaces (SVIs). By creating an SVI on the switch, the traffic is forwarded directly between VLANs on the switch, rather than forwarding to a dedicated layer 3 routing appliance. To use SVIs, the switch must be layer 3 capable, otherwise known as a Multi-layer switch.
To enable SVIs to allow inter-VLAN routing, the following steps are required:
-
Enable IP routing
-
Create the VLAN interfaces and assign IP addresses
-
No shut the interfaces
-
Assign out the VLANs as access ports to the relevant clients
-
Set client default gateways to point to the SVI IP addresses
-
Change the switchport connected to the router to a routed port and assign an IP address which is in the same subnet as the router